What is a Proxy Server?
A proxy server is a networking tool that acts as an intermediary – or middleman – between clients and servers on the Internet, such as a web browser and a web server. It verifies and forwards incoming client requests to other servers for further communication. While the proxy server’s primary role is to enhance security, it also offers additional functionality, such as improving performance and providing anonymity.
Techopedia Explains the Proxy Server Meaning
The meaning of a proxy server lies in its role as a middleman between clients and servers on the Internet. A client initially connects with a proxy server to send a request, such as accessing a file or opening a webpage. The proxy server filters and evaluates each IP address and request. The verified request is forwarded to the relevant server, which requests the service on behalf of the client.
A proxy server is used for many purposes, including:
- To provide internal system security.
- To speed up resource access.
- To enforce access control policies to restrict access to specific websites.
- To bypass special controls, such as parental or security controls.
- To detect and block malicious traffic.
- To log user activities, including websites visited and data transmitted.
- To circumvent regional restrictions.
- To allow websites to make requests to externally hosted resources when cross-domain. restrictions prohibit websites from linking to outside domains.
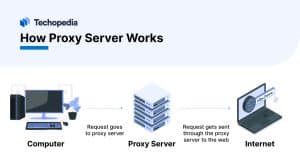
How Proxy Server Works
When a client device (e.g., a computer) requests a resource (e.g., a web page), it connects to the proxy server. The proxy server then forwards the request to the destination server. Once the proxy server receives a response, it relays it back to the client. Before relaying the response, the proxy server can perform various tasks, like caching, content filtering, or inspecting the response for malicious content.
What Protocols Do Proxy Servers Use?
Proxy Servers support various protocols – a set of rules and guidelines for communicating data.
Common protocols include the following:
- FTP (File Transfer Protocol)
- FTPS (FTP Secure)
- HTTP (Hypertext Transfer Protocol)
- HTTPS (HTTP Secure)
- SOCKS (Socket Secure)
- SSL/TLS (Secure Sockets Layer/Transport Layer Security)
Types of Proxy Servers
Different types of proxy servers provide specific functions with varying levels of performance and configuration options.
Types of proxy servers include:
- Anonymous Proxy
- Data Center Proxy
- Forward proxy
- Load Balancing Proxy
- Public proxy
- Reverse Proxy
- SOCKS Proxy
- SSL proxy
- Transparent proxy
- Web proxy
Proxy Server vs. VPN
Proxy servers and Virtual Private Networks (VPNs) are both used to enhance privacy and security, but they work differently.
| Proxy Server | Virtual Private Network (VPN) |
| Acts as an intermediary between a device and the Internet, rerouting traffic through the proxy server. | Encrypts traffic to and from a device, creating a secure tunnel between the user and the VPN server. |
| Faster performance for certain types of traffic. | Slower performance due to encryption. |
| Bypass geo-restrictions by hiding the IP address from destination servers, enabling anonymous browsing. | Bypass geo-restrictions by masking the IP address and routing the connection through servers located in different countries. |
| Used for specific tasks such as accessing region-restricted content or improving Internet performance through caching. | Used for more comprehensive security, especially for privacy and anonymity across all online activities. |
| Configured at the application level (i.e., within individual applications) or through network settings. | Operates at the network level. All network traffic leaving is encrypted and routed through the VPN server. |
Are Proxy Servers Safe?
The safety of proxy servers depends on several factors. Things to consider when evaluating the safety of proxy servers include:
Proxy Server Risks
Proxy servers, while offering benefits such as enhanced security, improved performance, and anonymity, also pose risks that users should be aware of.
Some proxy server risks include:
- Security vulnerabilities on misconfigured proxy servers.
- Malicious actors may distribute malware or phishing attacks.
- Bypassing content restrictions or blocked websites may violate regulations or policies.
- Lack of encryption leaves transmitted data vulnerable to interception.
- Degraded network performance, especially when handling large volumes of traffic.
Proxy Server Pros and Cons
Pros
- Enhanced security
- Faster web access
- Filter malicious content
- Geo-Restricted content access
- Online privacy and anonymity
Cons
- Compatibility issues with some applications
- Configuration complexity
- Legal and compliance issues
- Potential security vulnerabilities
- Privacy concerns due to logging
The Bottom Line
Proxy servers offer cost-effective security and anonymity for web browsing and content filtering. When used responsibly (i.e., in compliance with applicable laws and regulations), they can be a good choice for individuals or businesses. Keep in mind that the overall effectiveness depends on proper configuration, reflecting the importance of understanding the proxy server definition and its capabilities.
Businesses needing comprehensive protection for various online activities, including web browsing, email, and file transfers, as well as remote access or the ability to bypass censorship, should consider a VPN.